
As businesses continue to adopt cloud computing, there is a growing need for robust security measures to protect sensitive data and applications in the cloud.
CSPM (Cloud Security Posture Management) has emerged as a key technology to help organisations ensure the security and compliance of their cloud infrastructure. CSPM is an essential tool for businesses that operate in the cloud. With the rapid adoption of cloud computing, organizations need to ensure the security and compliance of their cloud infrastructure to protect sensitive data and applications from cyber threats. CSPM provides a unified view of cloud security by monitoring cloud environments for misconfigurations, vulnerabilities, and compliance violations. This allows businesses to proactively identify and address security risks, strengthen their cloud security posture, and ensure regulatory compliance.
However, CSPM as a SaaS (Software-as-a-Service) comes with several risks that businesses must be aware of to make informed decisions about their cloud security strategy.
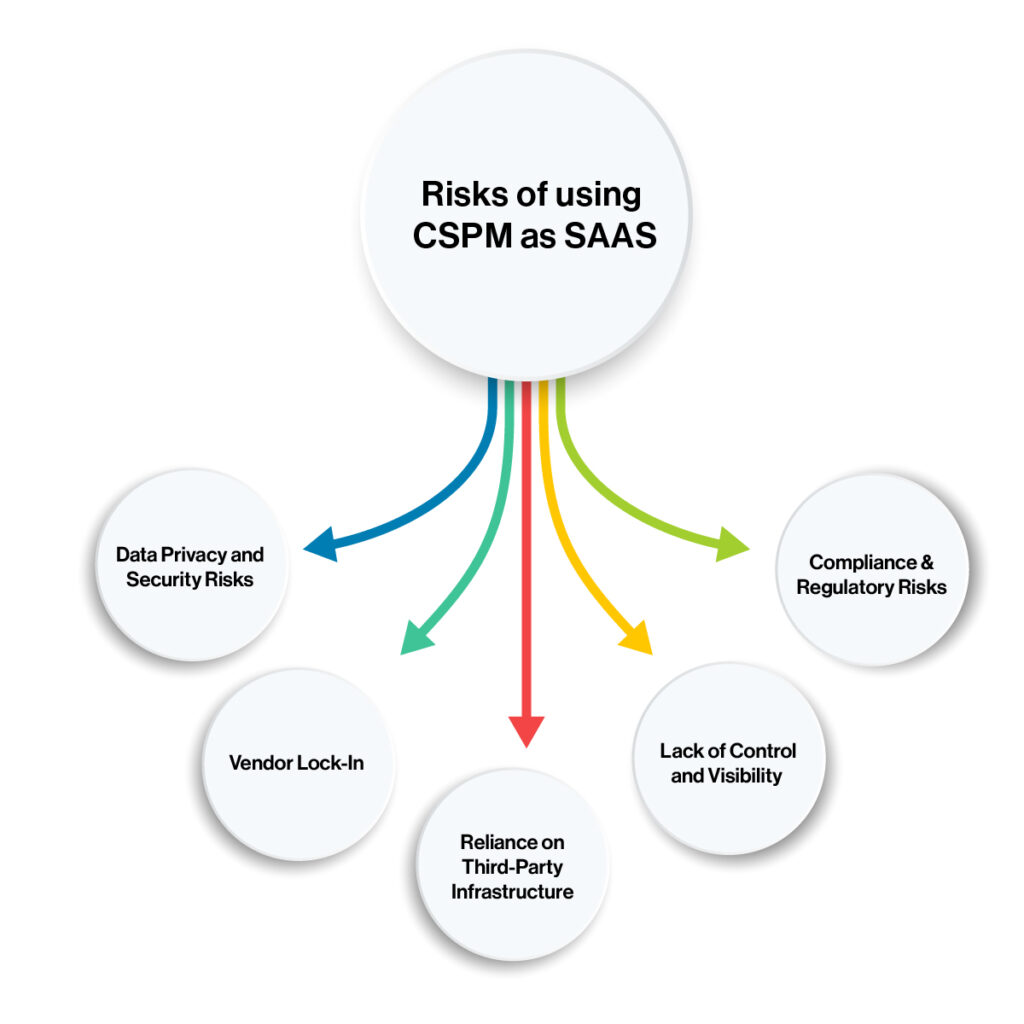
Data Privacy and Security Risks
As a SaaS offering, CSPM providers store sensitive data, such as access keys, user credentials, and network topologies, on their servers. This data must be secured from unauthorized access, data breaches, and cyber attacks. SaaS providers must ensure that their data centers are physically and logically secure and implement security controls such as encryption and access controls to protect customer data. In addition, customers must also ensure that they have proper security measures in place to prevent data breaches on their end.
Vendor Lock-In
CSPM SaaS providers may use proprietary tools and technologies, making it difficult for customers to switch to another provider. This can result in increased costs and reduced flexibility. Customers must ensure that they have a clear understanding of the CSPM provider’s technology stack and ensure that it aligns with their long-term cloud strategy. In addition, customers should establish clear exit strategies and backup plans in case they need to switch providers.
Reliance on Third-Party Infrastructure
CSPM SaaS providers typically rely on third-party infrastructure, such as public cloud platforms, for their services. This can introduce additional risks, such as data exposure and service disruption. Customers should ensure that the CSPM provider has proper security measures in place to protect their infrastructure, including network security, data encryption, and disaster recovery.
Lack of Control and Visibility
With CSPM as a SaaS, customers may have limited control and visibility into the security measures employed by the provider. This can result in reduced transparency and increased reliance on the provider for security. Customers should ensure that the CSPM provider has proper security controls in place, such as access controls, monitoring, and reporting, to provide visibility into their cloud security posture. In addition, customers should establish clear communication channels with the CSPM provider to ensure that they are notified of any security incidents or vulnerabilities.
Compliance & Regulatory Risks
CSPM SaaS providers must comply with various regulations and industry standards, such as GDPR and HIPAA. Customers must ensure that the provider complies with these regulations, as non-compliance can result in penalties and fines. In addition, customers must also ensure that their cloud infrastructure is compliant with these regulations, as they are ultimately responsible for the security of their data and applications in the cloud.
To mitigate these risks, customers should carefully evaluate CSPM SaaS providers, review their security practices and compliance certifications, and establish clear service level agreements (SLAs) to ensure that the provider meets their security and compliance requirements. Customers should also ensure that they have proper security measures in place to protect their infrastructure and data in the cloud. By taking a proactive approach to cloud security, businesses can ensure the safety and compliance of their cloud infrastructure and protect their sensitive data and applications from cyber threats.
Here are some steps that organizations can take to mitigate the risks associated with CSPM as a SaaS:
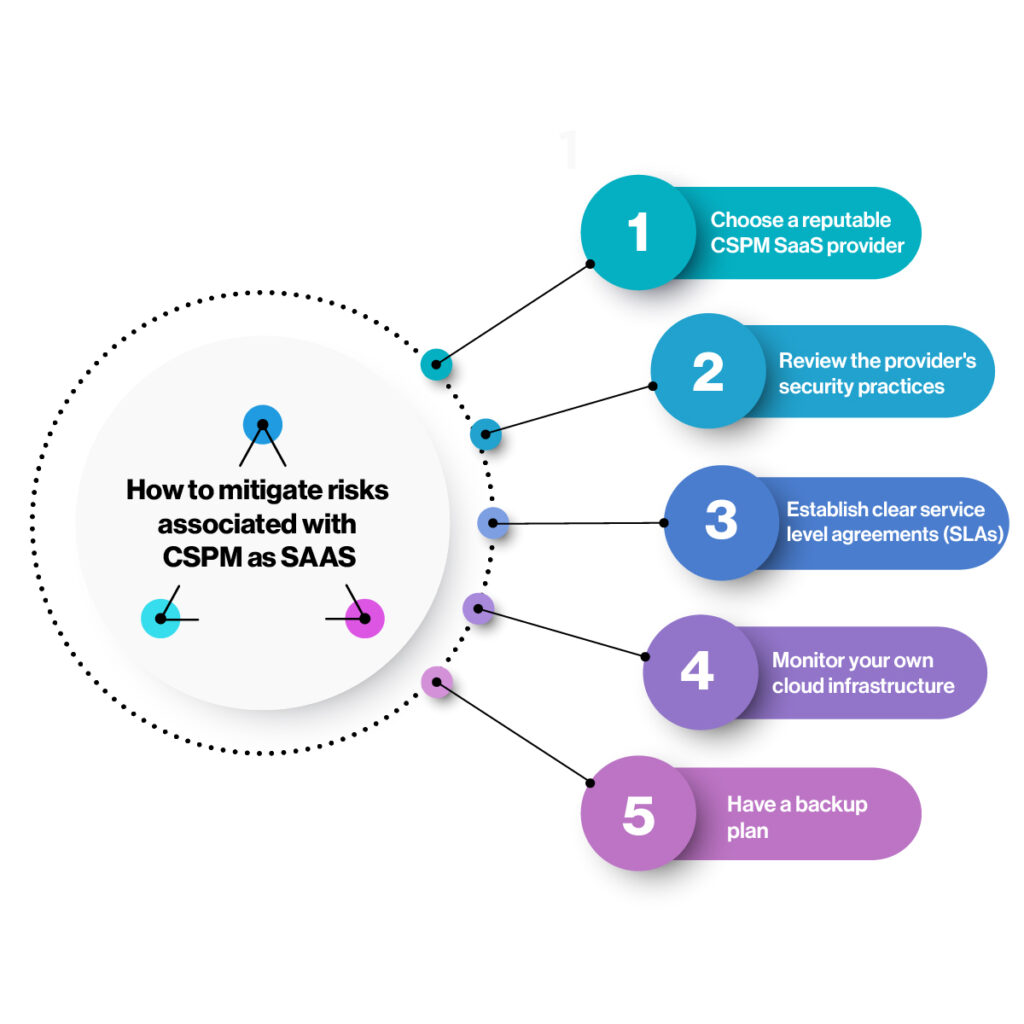
Choose a reputable CSPM SaaS provider: When selecting a CSPM SaaS provider, it is crucial to do your research and choose a reputable provider with a proven track record in cloud security. Look for providers that have industry certifications, such as SOC 2 or ISO 27001, and a strong reputation for security and reliability.
Review the provider’s security practices: It is important to review the CSPM provider’s security practices and ensure that they have adequate measures in place to protect customer data. This includes physical and logical security controls, encryption of sensitive data, and access controls to limit unauthorised access.
Establish clear service level agreements (SLAs): To ensure that the CSPM provider meets your security and compliance requirements, it is essential to establish clear SLAs that define the provider’s responsibilities and performance metrics. This includes requirements for data privacy, security, availability, and response time to security incidents.
Monitor your own cloud infrastructure: While CSPM can provide visibility into your cloud security posture, it is important to monitor your own cloud infrastructure and implement security measures to protect against potential threats. This includes regular vulnerability scans, access control management, and continuous monitoring for security incidents.
Have a backup plan: In the event of a security incident or data breach, it is important to have a backup plan in place to ensure business continuity. This includes regularly backing up data and having a plan in place for disaster recovery and business continuity.
In summary, mitigating the risks associated with CSPM as a SaaS requires a proactive approach to cloud security. By choosing a reputable provider, reviewing their security practices, establishing clear SLAs, monitoring your own cloud infrastructure, and having a backup plan in place, businesses can minimize the risks associated with CSPM as a SaaS and ensure the security and compliance of their cloud infrastructure.